Last Updated on 2 months by Sachin G
As a Linux system administrator or DevOps professional, managing SELinux modes remotely can be time-consuming, especially across multiple nodes. This guide walks through how to disable or enforce SELinux using Ansible, and reboot the host if required—an essential skill for anyone working with Linux automation, be it on CentOS, Red Hat Enterprise Linux ( RHEL ), Rocky Linux, or Fedora.
Do you want to disable or enable (enforce) SELinux mode on host machines through the ansible-playbook? This blog post article I am writing to handle real-world problems, shares the cause and offers practical, actionable steps using Ansible playbooks to change the mode of the SELinux type. SELinux is an important security feature of Linux. There are three values in SELinux: Enforcing, Permissive, and Disabled. The main configuration file of SELinux security is /etc/selinux/config .
Learn Smarter. Level Up Faster →
Want to master Linux, DevOps, Ansible, or Cloud workflows the smart way? I’ve curated a list of top-rated, real-world Udemy courses — based on student reviews and practical feedback.
Visit the Recommended Courses page to explore and enroll in courses trusted by the community.
See Curated Courses →What Are Common SELinux Modes in Linux?
Enforcing: This shows the security policy is enforced.
Permissive: This value shows the security policy only shows warning instead of enforced.
Disabled: It means the policy is not loaded in the kernel or disabled in the conditions.
Use getenforce to check the current mode and setenforce to change temporarily.
SELinux is a kernel-based security module, So when you make a change from Disabled to Enforcing or Enforcing to Disabled, you should always reboot your machine because the system reads the configuration file at boot time.
- The playbook is tested on CentOS Stream 9 Linux. All the identical machines with CentOS 9.
- Before executing this on the production environment, you should check on your testing environment.
- You should dry run or test run before executing through ansible-playbook -C PlaybookName.yml
- A version of Ansible that I used is Ansible [core 2.14.2] or Ansible-navigator 2.2.0 Platform.
Why Would You Want to Disable or Enable SELinux Using Ansible?
System admins often disable SELinux to avoid permission-related issues, especially when deploying new applications or troubleshooting services. On the flip side, enforcing SELinux helps enhance security. Using Ansible automation makes this process consistent and scalable.
Problem:
- Manual SELinux updates require logging into each host.
- Changes
SELinux modeoften need a reboot to take effect.
- Risk of human error when editing
selinux config file.
Solution:
- Set desired SELinux modes (disabled, permissive, enforcing)
- Modify the
/etc/selinux/config
- Reboot host automatically, if required
How to Disable SELinux with Ansible Playbook?
Disabling SELinux can be done via a simple Ansible playbook by modifying the configuration and running a reboot task. Before executing any playbook,you should always test on your environment or dry run.
- name: Disable SELinux on remote host
hosts: all
become: yes
tasks:
- name: Set SELinux to disabled in config file
replace:
path: /etc/selinux/config
regexp: '^SELINUX=.*'
replace: 'SELINUX=disabled'
- name: Reboot the system for SELinux to take effect
reboot:
reboot_timeout: 300Below is another playbook I wrote for this task. Through this playbook, if the system is already in the desired state or disabled, then after executing this playbook, the managed host machine will not be rebooted. This playbook only reboots when changes occur in the configuration file.
---
- name: Ansible Playbook for disabling SELinux and Reboot .
hosts: srv1.example.com
handlers:
- name: reboot server
command: systemctl reboot
tasks:
- name: Disabling SELinux
ansible.posix.selinux:
state: disabled
register: selinuxdisabled
- name: Print the changes in Configurtion file
ansible.builtin.command: grep SELINUX /etc/sysconfig/selinux
register: sevalue
- ansible.builtin.debug:
var: sevalue.stdout_lines
- name: Wait for 5 Second and Reboot
shell: "sleep 5 && reboot"
async: 1
poll: 0
when: selinuxdisabled is changed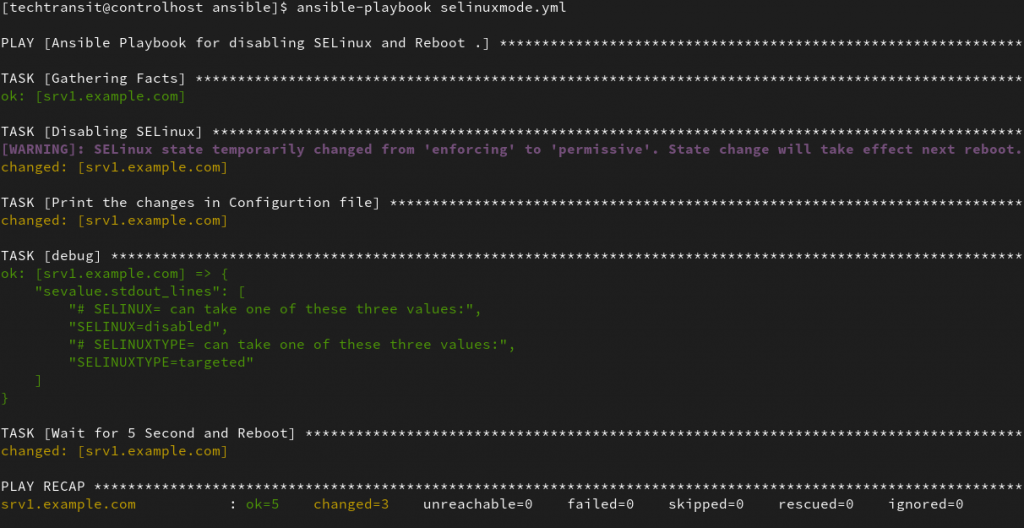
Best Practices:
- Always test on non-production systems first.
- Use tags and handlers for better control.
- Document changes and commit to version control.
How to Enforce SELinux via Ansible?
To enable enforcing mode, update both the config file and apply the setting immediately using setenforce.
- name: Enforce SELinux using Ansible
hosts: all
become: yes
tasks:
- name: Change SELinux mode to enforcing in config
replace:
path: /etc/selinux/config
regexp: '^SELINUX=.*'
replace: 'SELINUX=enforcing'
- name: Apply enforcing mode live
command: setenforce 1
- name: Reboot to apply SELinux enforcement
reboot:Below is another playbook I wrote for this task for enforcing the selinux. So this second playbook.
---
- name: Ansible Playbook for enabling SELinux and Reboot .
hosts: srv1.example.com
handlers:
- name: reboot server
command: systemctl reboot
tasks:
- name: Enabling SELinux
ansible.posix.selinux:
state: enforcing
policy: targeted
register: selinuxdisabled
- name: Print the changes in Configurtion file
ansible.builtin.command: grep SELINUX /etc/sysconfig/selinux
register: sevalue
- ansible.builtin.debug:
var: sevalue.stdout_lines
- name: Wait for 5 Second and Reboot
ansible.builtin.shell: "sleep 5 && reboot"
async: 1
poll: 0
when: selinuxdisabled is changed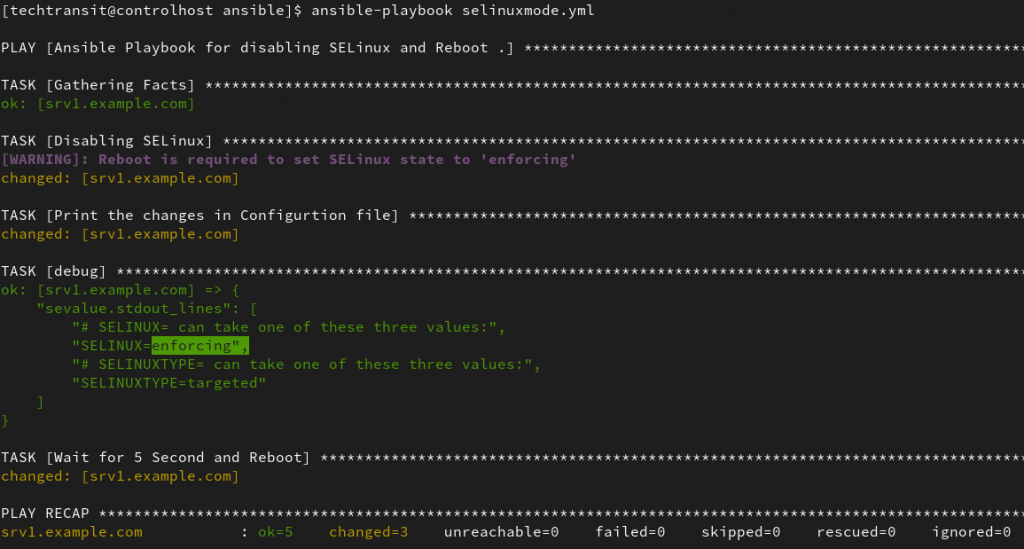
Always use
getenforceafter reboot to verify.
Can You Reboot Linux Host After SELinux Change Using Ansible?
Yes, Ansible provides a dedicated reboot module that allows clean and controlled reboots after applying SELinux changes.
- name: Automatically reboot after SELinux config change
reboot:
reboot_timeout: 300
Combine it with conditionals if you want to reboot only when SELinux changes.
Here I am ensuring in my playbook the configuration files are changing and printing the output in the playbook at run time. After printing the output the machine will reboot.
Bonus Tips: SELinux Management Best Practices
- Use
getenforceandsetenforcefor temporary changes.
- Modify
/etc/selinux/configfor persistent changes.
- Always monitor logs under
/var/log/audit/audit.log.
- Integrate SELinux mode validation in CI/CD pipeline using
Ansible by Red Hat.
Yes, use host variables to define SELinux mode (disabled, permissive, enforcing) per server.
Changes to /etc/selinux/config won’t take effect until after reboot—current mode remains until system restarts.
Disabling reduces security. It’s recommended only for debugging or if using alternate security layers like AppArmor.

I’m Sachin Gupta — a freelance IT support specialist and founder of techtransit.org. I’m certified in Linux, Ansible, OpenShift (Red Hat), cPanel, and ITIL, with over 15 years of hands-on experience. I create beginner-friendly Linux tutorials, help with Ansible automation, and offer IT support on platforms like Upwork, Freelancer, and PeoplePerHour. Follow Tech Transit for practical tips, hosting guides, and real-world Linux expertise!

