Last Updated on 7 months by Sachin G
We have got many changes in Red Hat Enterprise Linux / CentOS , one of the many changes GRUB 2 version. Reset the password through single user mode we are using in RHEL 5 and RHEL 6 version but here it will be different from older versions.
We may need to reset the root password if we forget it, or if it has been stolen or changed by someone else. In such cases, we won’t be able to log in or access the system to make any changes, so resetting the password becomes necessary. So Don’t worry! with a few steps , you can reset the root password and regain full access to your linux system. In this post i am usnig single-user mode method.
Use below procedure carefully and mistake can make your machine unstable, first try l test machine on your own risk.
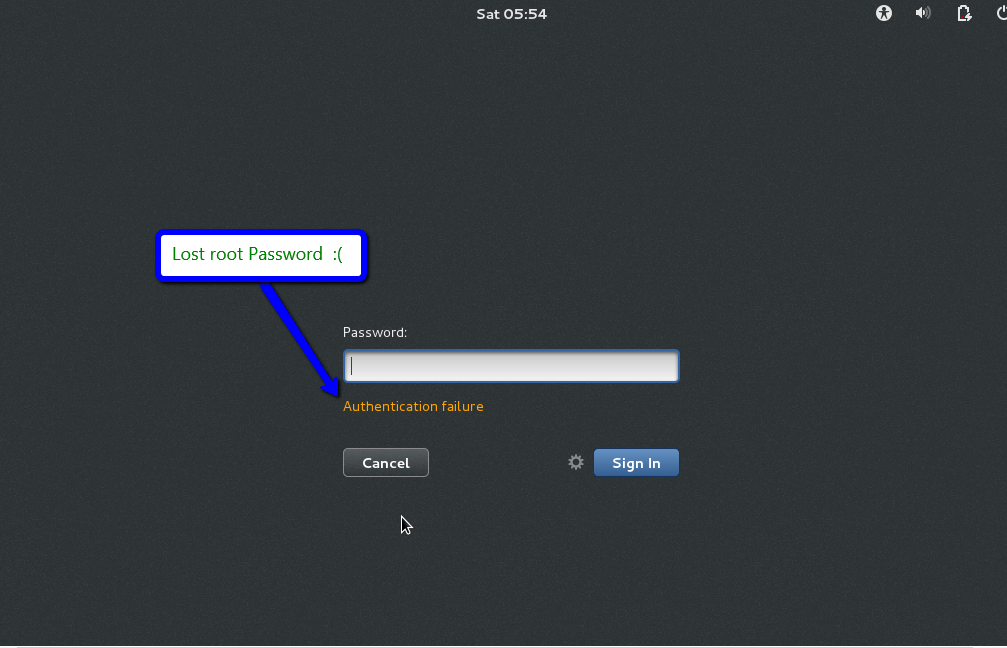
Show Forget root password and Reboot the system
Here I am showing the screen of trying to login through GUI in Linux box and not getting success via root in login through GUI , same will be implement as command line interface.
Booting into Single-User Mode
In new version of GRUB , we will use single-user mode in rescue mode , In GRUB2 we have the Rescue Mode / Emergency mode in new version , which makes it perfect for password recovery.
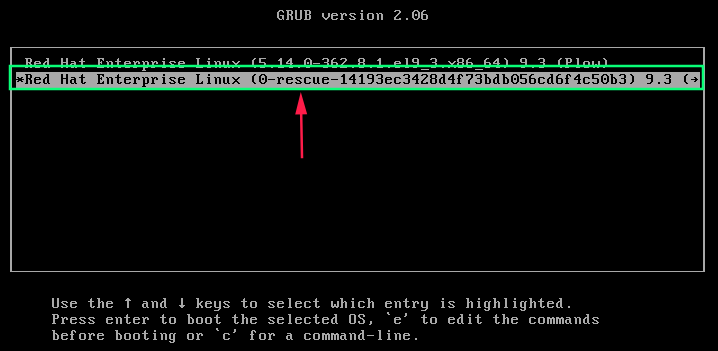
First start or reboot your machine and wait for GRUB 2 booting menu screen , it will show in image below and press “e” edit key to edit the grub 2 menu option after grub 2 loaded .
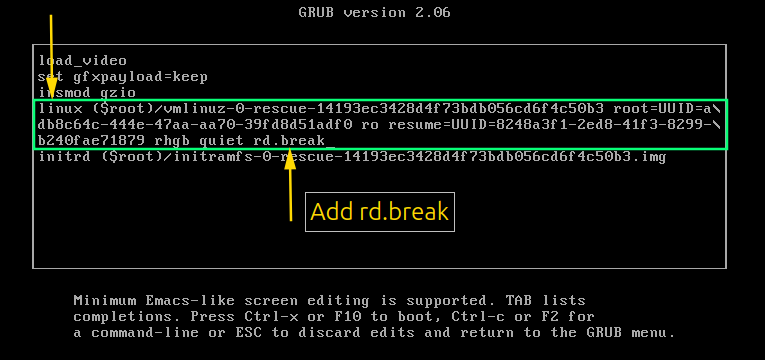
Look for the line starting with linux . This line specifies the kernel parameters for booting.Add the rd.break text at the end of the line press ctrl+x to boot or start the process.
Resetting the Root Password
Now the Emergency shell mode or rescue shell mode will available for reset the password .
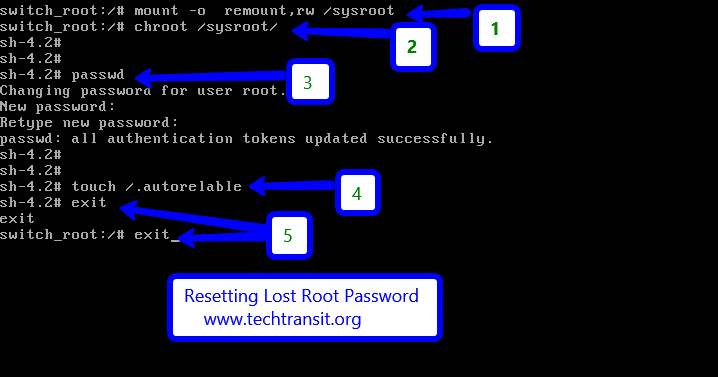
First we will remount the sysroot file system in read and write mode . Then use chroot to got into a chroot jait at /sysroot through below commands .
# mount –o remount,rw /sysroot
Now, access the root environment:
# chroot /sysroot
Now we will give passwd command in the command line and press same password twice for reset root password.
In the Last point make sure that all unlabeled files ( including shadow ) get relabeled during boot with below command.
# touch /.autorelabel
Type exit two times after run autoreleble activity. The first will exit the chroot jail and the second will exit the initramfs debug shell.
Find below all the commands history which we use to reset the password.
Now we have to reset the password of root . After exit two times system will boot again and check given root credentials is working properly.
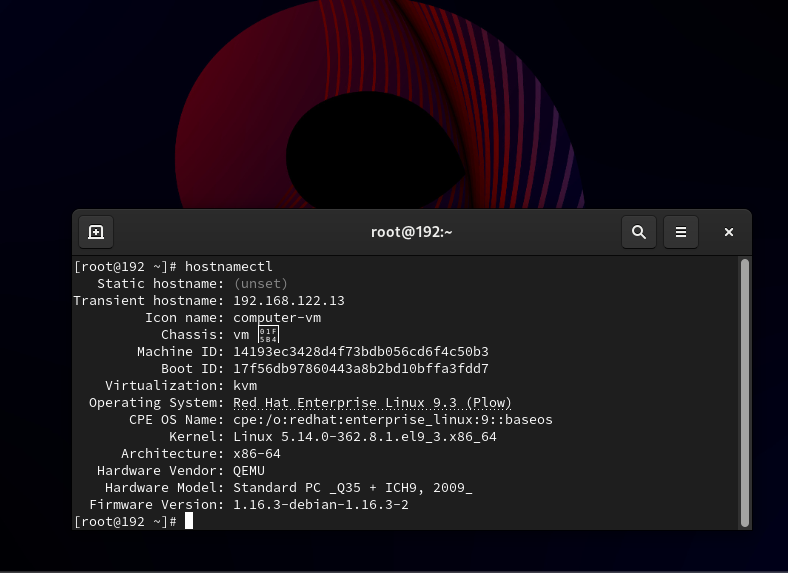
I have got root screen .. 🙂 . The process itself wasn’t too difficult, but it definitely reminded me how important it is to keep secure and memorable passwords. I felt a mix of satisfaction and a bit of frustration that I even had to go through this, but in the end, it was a good learning experience .

I am a professional freelance contributor and the founder of Tech Transit. I hold certifications in Linux, Ansible, and OpenShift from Red Hat, as well as CPanel and ITIL certifications. With a passion for education, culture, and community, I love writing and sharing knowledge. Since 2009, I’ve been actively using, setting up, supporting, and maintaining Linux systems. Linux truly rocks!