Last Updated on 1 year by Sachin G
If you are using the Linux operating system, might be more vulnerable than you think. Intruders love exploiting weaknesses and another common technique is privilege escalation. This makes them take control of your system and it can potentially steal data, add or install malware, or initiate attacks on others. We can secure special permissions for important files, which can prevent intruders from using important files for privilege escalation.
Understanding Special Permissions
Special permission can be useful in some scenarios, but they can also pose security risks if not managed properly. intruders often target files with special permissions to execute malicious code and escalate their privileges on the system. In Linux systems, special permission is suid, sgid, and a sticky bit to give additional privileges to users and processes.
The “suid” permission, also known as the Set User ID, grants users the ability to execute a file with the permissions of the file owner, regardless of who is running it. On the other hand, the “sgid” permission, or Set Group ID, enables files and directories to inherit the group ownership of their parent directory, ensuring consistent group ownership throughout the directory structure.
Finding Important Files
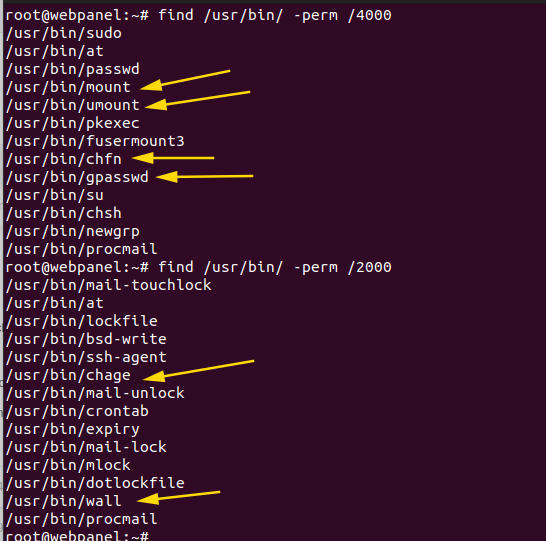
First, we should know which files are critical and contain sensitive data to the system operation. This can be system configuration files, system binaries, and files containing user credentials or sensitive information. Mostly binary and configuration on /usr/bin /usr/sbin and /etc folder. Let’s look at how we can find files that have SUID and SGID through the find command. Read about the find command, Just Read it Find command.
I am Checking for files with suid and sgid permissions.
The below find command syntax according to permission is
find search_directory -perm /permission
In my case I search in /usr/bin directory suid and sgid permission, and many files are showing but some important “chage, gpasswd wall, chfn, chsh, newgrp, mount, umount”. where we will remove special permissions.
Steps to Remove Unnecessary Special Permissions
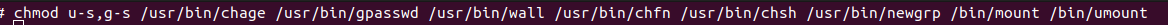
To remove special permissions from a file, you can use the chmod command followed by the appropriate flags. For example, to remove the suid permission from a file, use the command chmod u-s filename. Similarly, to remove the sgid permission, use chmod g-s filename. For files with the sticky bit set, use chmod o-t filename.
chmod u-s/g-s [filename]
The below screenshot shows, I remove some special permission on selected files. you should be an expert in Linux to identify which files you should remove with special permission.
Be careful when changing permissions. Incorrect changes could affect system functionality. Research specific file permissions before making changes.

I am a professional freelance contributor and the founder of Tech Transit. I hold certifications in Linux, Ansible, and OpenShift from Red Hat, as well as CPanel and ITIL certifications. With a passion for education, culture, and community, I love writing and sharing knowledge. Since 2009, I’ve been actively using, setting up, supporting, and maintaining Linux systems. Linux truly rocks!

